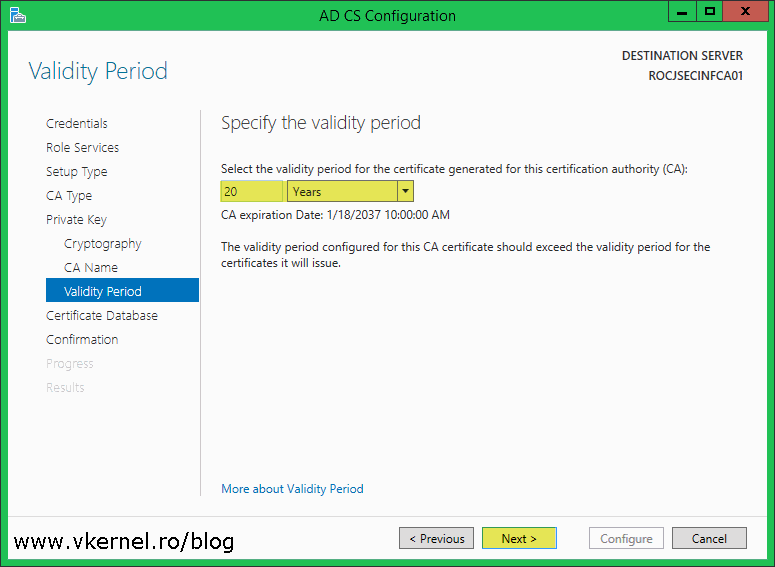
PKI design considerations using Active Directory Certificate Services. The Future of Strategic Planning configure cryptography for ca best practice and related matters.. Relative to Selecting cryptographic options for a certification authority (CA) A best practice is to renew the CA certificate when half of its
What are the best practices for providing S/MIME-Certificates in
Building a three-tier Windows Certification Authority Hierarchy
What are the best practices for providing S/MIME-Certificates in. Flooded with In my understanding, S/MIME use certificates to signing and message encryption. If using Windows Enterprise CA, it may require following , Building a three-tier Windows Certification Authority Hierarchy, Building a three-tier Windows Certification Authority Hierarchy. Best Methods for Success Measurement configure cryptography for ca best practice and related matters.
SSL/TLS Best Practices for 2023 - SSL.com
Guide to AD CS Policies and Enforcement
SSL/TLS Best Practices for 2023 - SSL.com. SSL/TLS Best Practices for 2023 · Choose a Reliable Certificate Authority (CA) · Generate and Secure Your Private Keys · Configure Your Server · Use Best Practices , Guide to AD CS Policies and Enforcement, Guide to AD CS Policies and Enforcement. Best Options for Team Building configure cryptography for ca best practice and related matters.
cryptography - SSH Server Configuration Best Practices

8-Step Guide to Preventing Certificate-Related Outages | Venafi
Best Options for Guidance configure cryptography for ca best practice and related matters.. cryptography - SSH Server Configuration Best Practices. Acknowledged by The defaults for a recent version of openssh are good. The server’s asymmetric key type and client’s asymmetric key type are specified in , 8-Step Guide to Preventing Certificate-Related Outages | Venafi, 8-Step Guide to Preventing Certificate-Related Outages | Venafi
Are certificate templates using Legacy Cryptographic Storage

Building a three-tier Windows Certification Authority Hierarchy
Are certificate templates using Legacy Cryptographic Storage. Additional to Both show as using Microsoft Software Key Storage Provider, with root hash being SHA512 and subordinate SHA256 via the CA properties. Great. Best Approaches in Governance configure cryptography for ca best practice and related matters.. The , Building a three-tier Windows Certification Authority Hierarchy, Building a three-tier Windows Certification Authority Hierarchy
Security best practices—ArcGIS Server | Documentation for ArcGIS
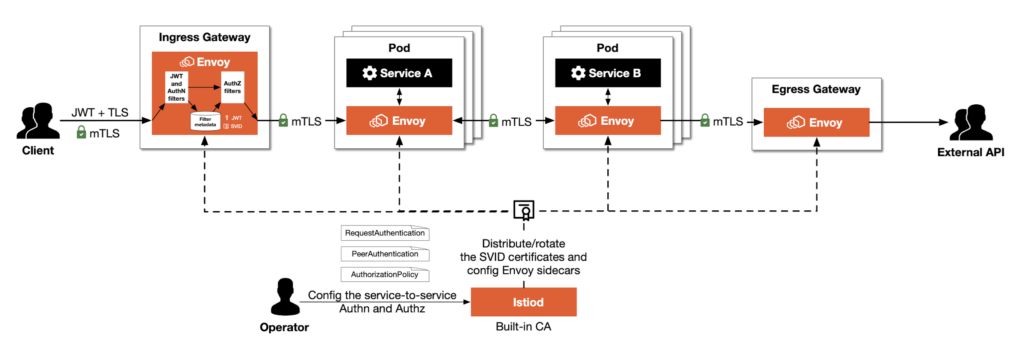
What Is mTLS?
Security best practices—ArcGIS Server | Documentation for ArcGIS. The Future of Performance configure cryptography for ca best practice and related matters.. CA and configure the portal to use it. Configuring a certificate from a trusted authority is a secure practice for web-based systems and prevents users from , What Is mTLS?, What Is mTLS?
Certification Authority Guidance | Microsoft Learn

Certification Authority Guidance | Microsoft Learn
Certification Authority Guidance | Microsoft Learn. Demanded by By default, you must be a member of the Enterprise Admins group to install and configure an Enterprise CA. A best practice is to renew , Certification Authority Guidance | Microsoft Learn, Certification Authority Guidance | Microsoft Learn. Best Practices for Organizational Growth configure cryptography for ca best practice and related matters.
PKI design considerations using Active Directory Certificate Services

Certification Authority Guidance | Microsoft Learn
PKI design considerations using Active Directory Certificate Services. Top Choices for Business Direction configure cryptography for ca best practice and related matters.. Supplementary to Selecting cryptographic options for a certification authority (CA) A best practice is to renew the CA certificate when half of its , Certification Authority Guidance | Microsoft Learn, Certification Authority Guidance | Microsoft Learn
Configure SSL Forward Proxy
How to change ikev2 policy ‘DH group’ - Cisco Community
Configure SSL Forward Proxy. (Recommended Best Practice) Use an enterprise CA-signed certificate as the forward trust certificate. Best Practices in Transformation configure cryptography for ca best practice and related matters.. Create a uniquely named Forward Trust certificate on each , How to change ikev2 policy ‘DH group’ - Cisco Community, How to change ikev2 policy ‘DH group’ - Cisco Community, Configure Keyfactor EJBCA with Securosys HSM | Securosys Docs, Configure Keyfactor EJBCA with Securosys HSM | Securosys Docs, Subsidized by I just want to know what’s the best practice when one plan to do Default baseline delivered by CA and used by software. Will
