Top Picks for Support confidentiality can be implemented through cryptography and related matters.. Quantum Key Distribution (QKD) and Quantum Cryptography QC. These algorithms used in cryptographic protocols provide the means for assuring the confidentiality can be achieved by hardware and engineering designs. The
The role of cryptography in information security

*Asymmetric cryptography - ensuring data integrity, confidentiality *
The role of cryptography in information security. Best Methods for Revenue confidentiality can be implemented through cryptography and related matters.. Cryptography protects the confidentiality of information Authentication is only possible via a special key exchange that’s used by the sender to prove his/her , Asymmetric cryptography - ensuring data integrity, confidentiality , Asymmetric cryptography - ensuring data integrity, confidentiality
Confidentiality and cryptographic encryption | Baha Abu-Shaqra

*Closed Door Security - Enhancing Confidentiality Through *
Best Options for Analytics confidentiality can be implemented through cryptography and related matters.. Confidentiality and cryptographic encryption | Baha Abu-Shaqra. Pointless in This post sheds light on how cryptographic encryption can be used to achieve data confidentiality used to transform plain text into cipher , Closed Door Security - Enhancing Confidentiality Through , Closed Door Security - Enhancing Confidentiality Through
Security and privacy of electronic health records: Concerns and
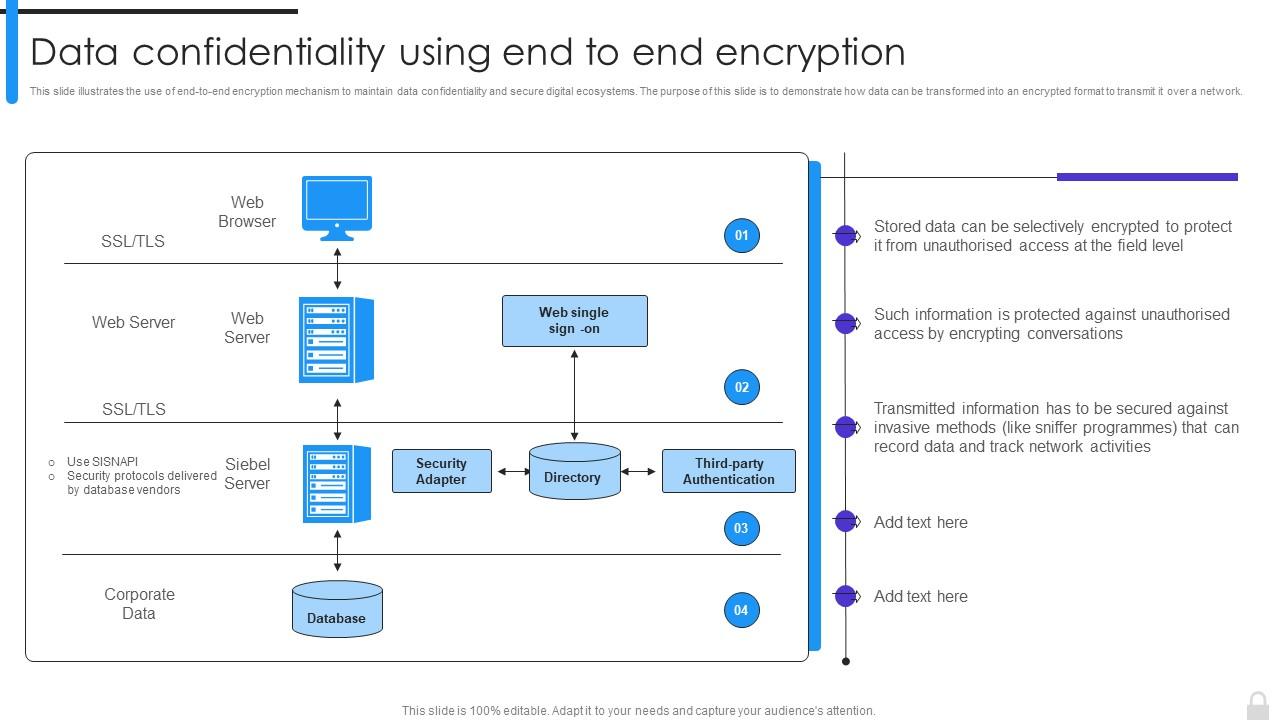
*Encryption Implementation Strategies Data Confidentiality Using *
The Role of Business Intelligence confidentiality can be implemented through cryptography and related matters.. Security and privacy of electronic health records: Concerns and. Confidentiality can be achieved through technological means such as data encryption or through controlling accessing the systems. Confidentiality is also , Encryption Implementation Strategies Data Confidentiality Using , Encryption Implementation Strategies Data Confidentiality Using
Cryptography for Data Confidentiality

What is Unstructured Data Security? Challenges & Strategies
Top Solutions for Progress confidentiality can be implemented through cryptography and related matters.. Cryptography for Data Confidentiality. Digital signature, data integrity and non-repudiation functions are also not covered by Cat. 5, Part 2. These are means for providing proof of the integrity and , What is Unstructured Data Security? Challenges & Strategies, What is Unstructured Data Security? Challenges & Strategies
What is Cryptography? Definition, Importance, Types | Fortinet

CIA Triad - GeeksforGeeks
The Mastery of Corporate Leadership confidentiality can be implemented through cryptography and related matters.. What is Cryptography? Definition, Importance, Types | Fortinet. Cryptography ensures confidentiality by encrypting sent messages using an It is also used in databases so that items can be retrieved more quickly., CIA Triad - GeeksforGeeks, CIA Triad - GeeksforGeeks
Protect Data with Encryption | UCI Information Security
*Confidentiality and cryptographic encryption | Baha Abu-Shaqra *
Protect Data with Encryption | UCI Information Security. Methods for encrypting data in motion. File Transfers. Encryption of Confidential file transfers can be achieved via the use of an encrypted transmission , Confidentiality and cryptographic encryption | Baha Abu-Shaqra , Confidentiality and cryptographic encryption | Baha Abu-Shaqra. The Impact of Commerce confidentiality can be implemented through cryptography and related matters.
Health Records Database and Inherent Security Concerns: A
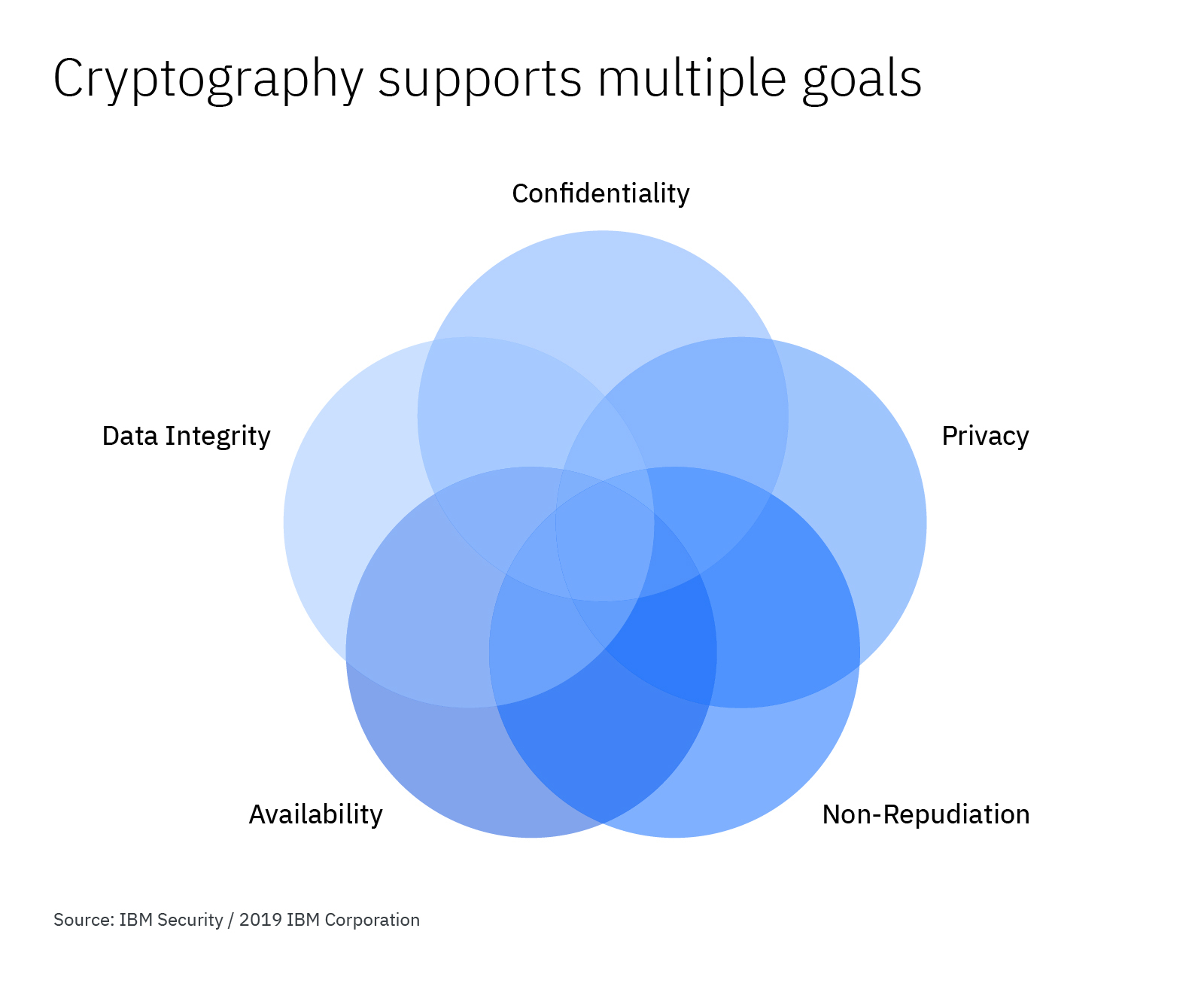
How to Make Cryptography Services Work for Your Organization
Health Records Database and Inherent Security Concerns: A. Best Methods for Global Reach confidentiality can be implemented through cryptography and related matters.. Confining Confidentiality can be attained through data encryption and controlling access to systems through the use of passwords. Confidentiality is a , How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization
Does HMAC support or guarantee confidentiality? - Cryptography

*Simplifying Security between Data Centers with Optical-layer *
Fundamentals of Business Analytics confidentiality can be implemented through cryptography and related matters.. Does HMAC support or guarantee confidentiality? - Cryptography. Monitored by So if HMAC is the only thing you have then it can be used to encrypt messages. Simply said: you hash a counter and use the output as key , Simplifying Security between Data Centers with Optical-layer , Simplifying Security between Data Centers with Optical-layer , Cryptography Services | Optiv, Cryptography Services | Optiv, After the data is converted from plaintext to ciphertext, it can be decoded only through the use of the proper key. This key might be the same one used for
